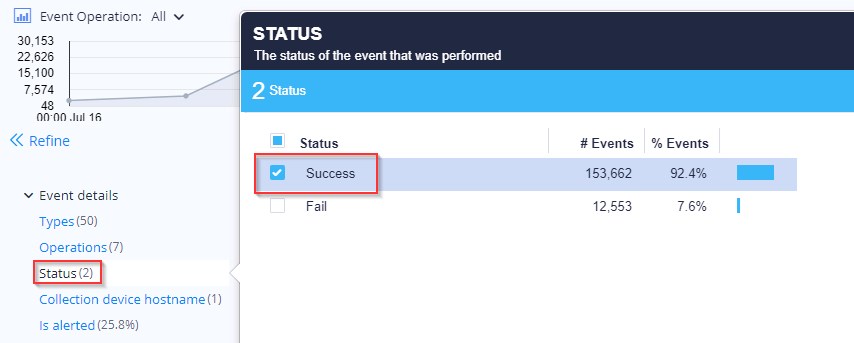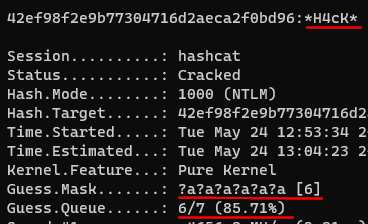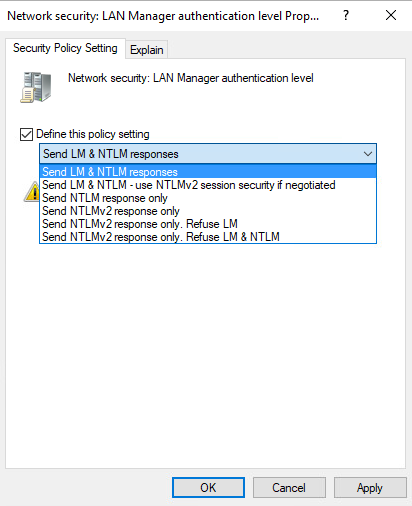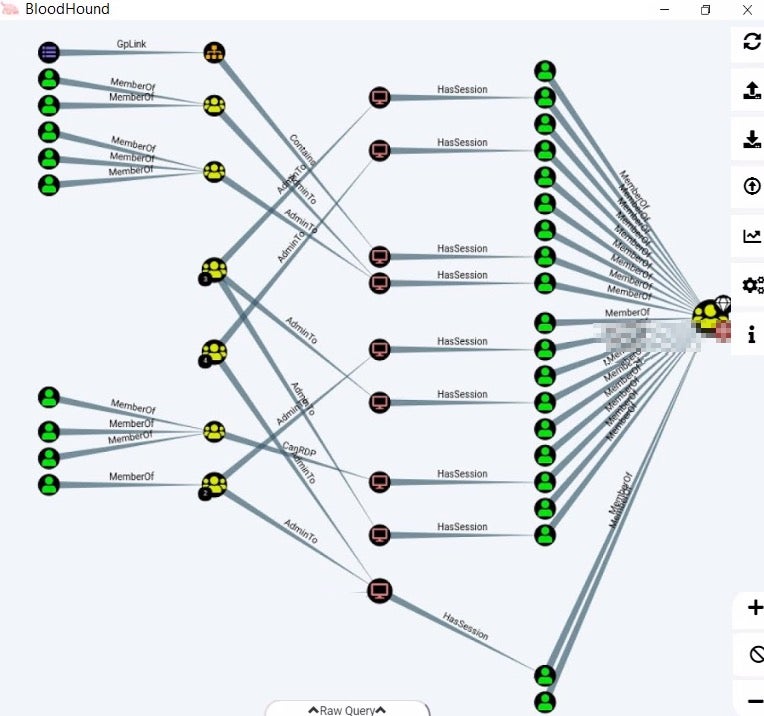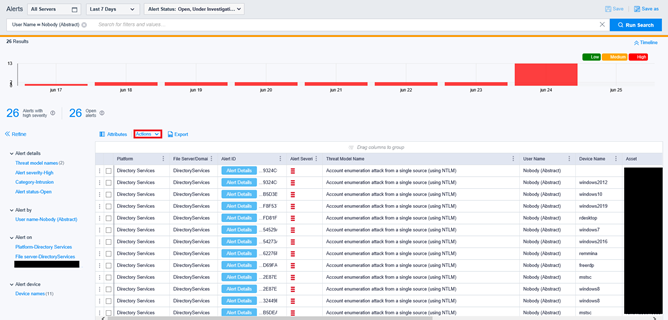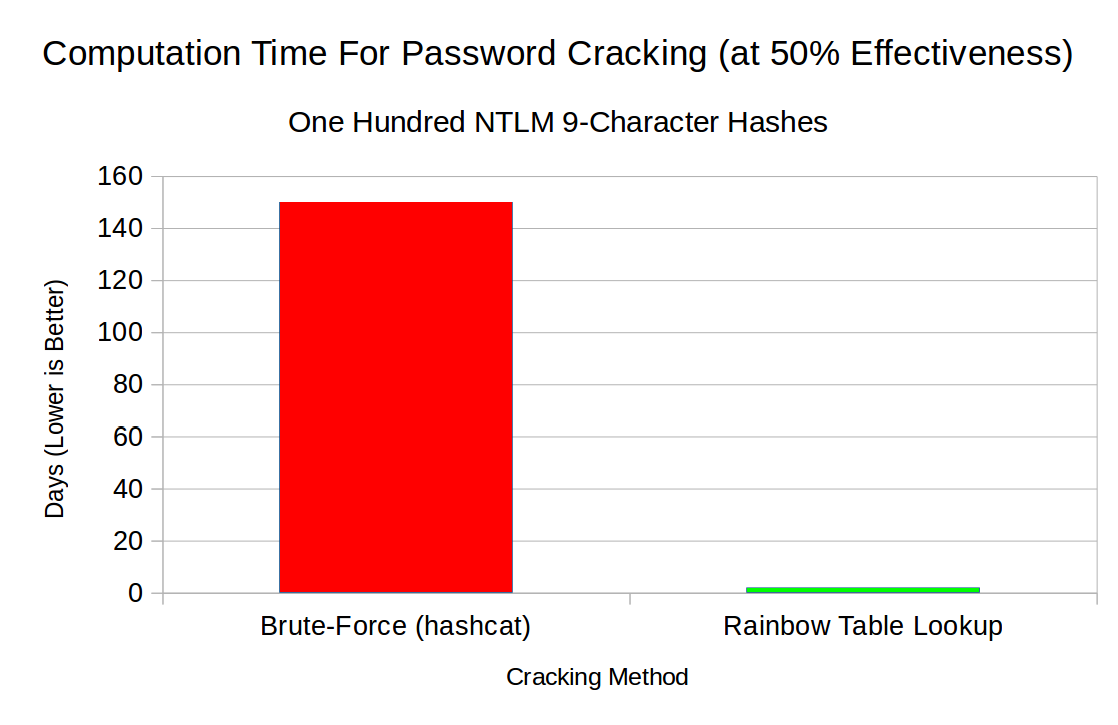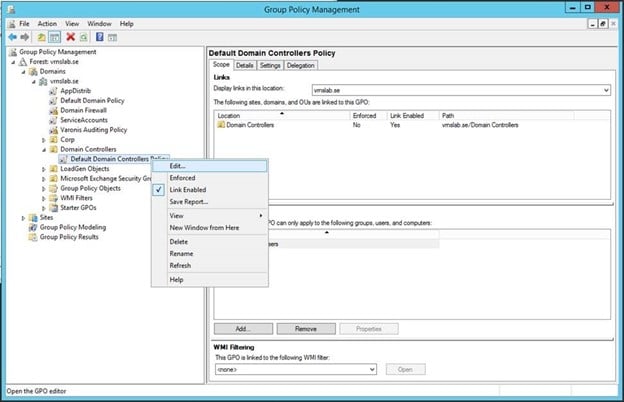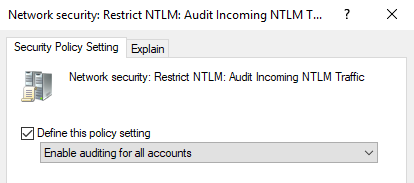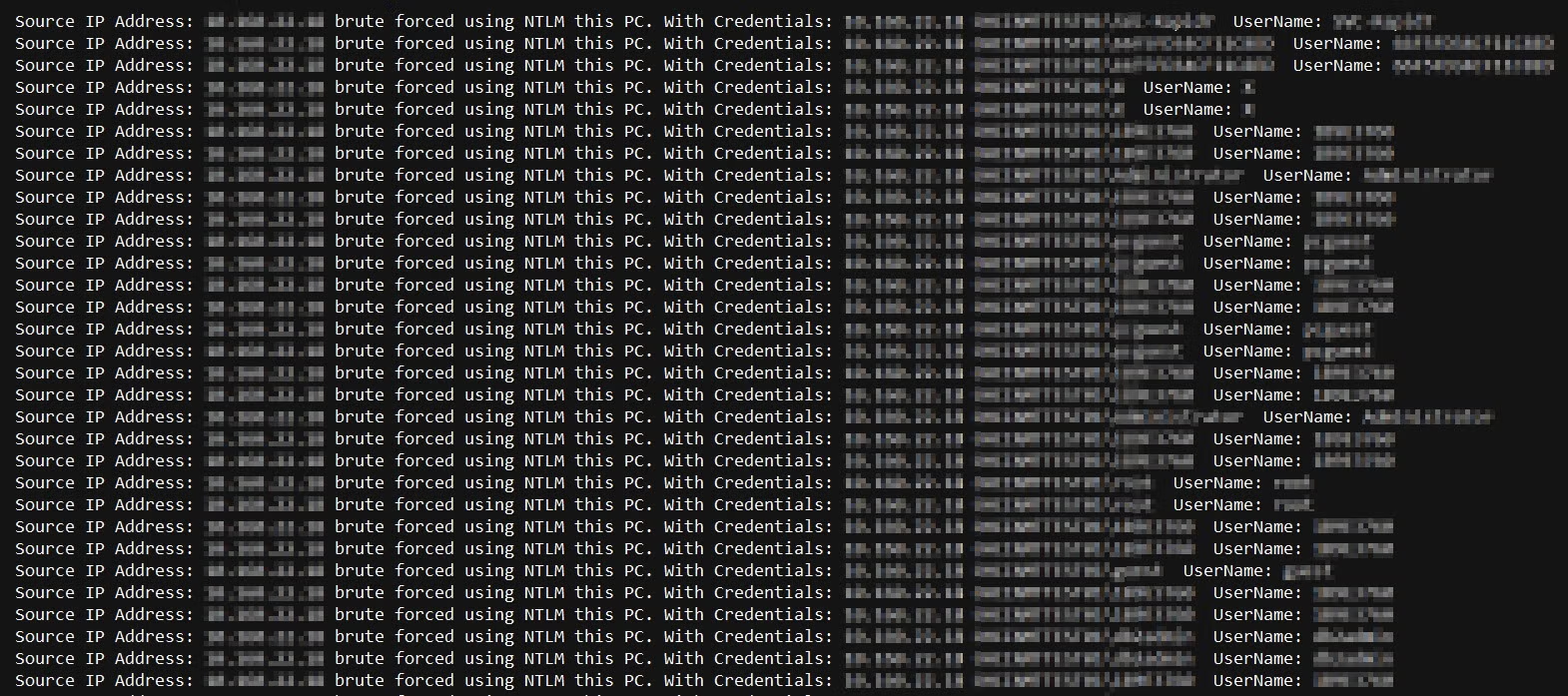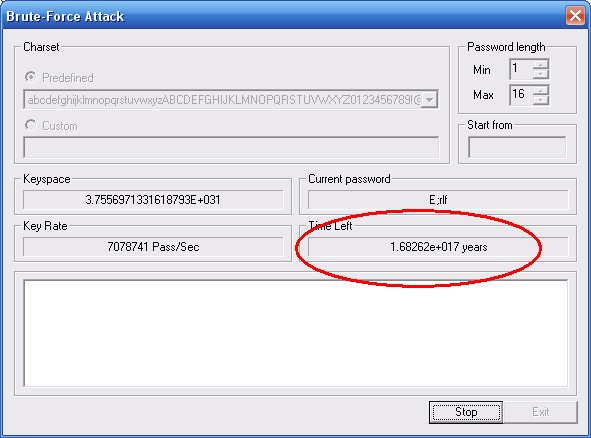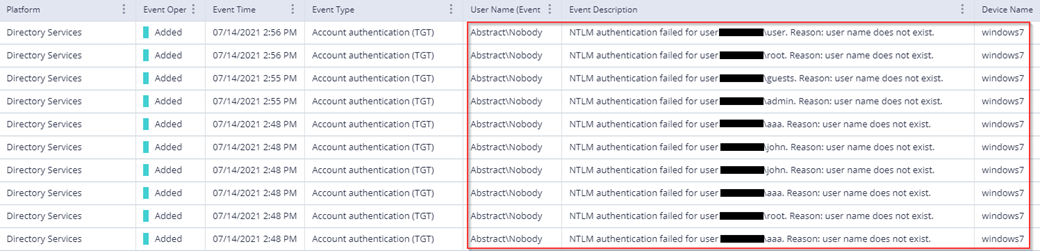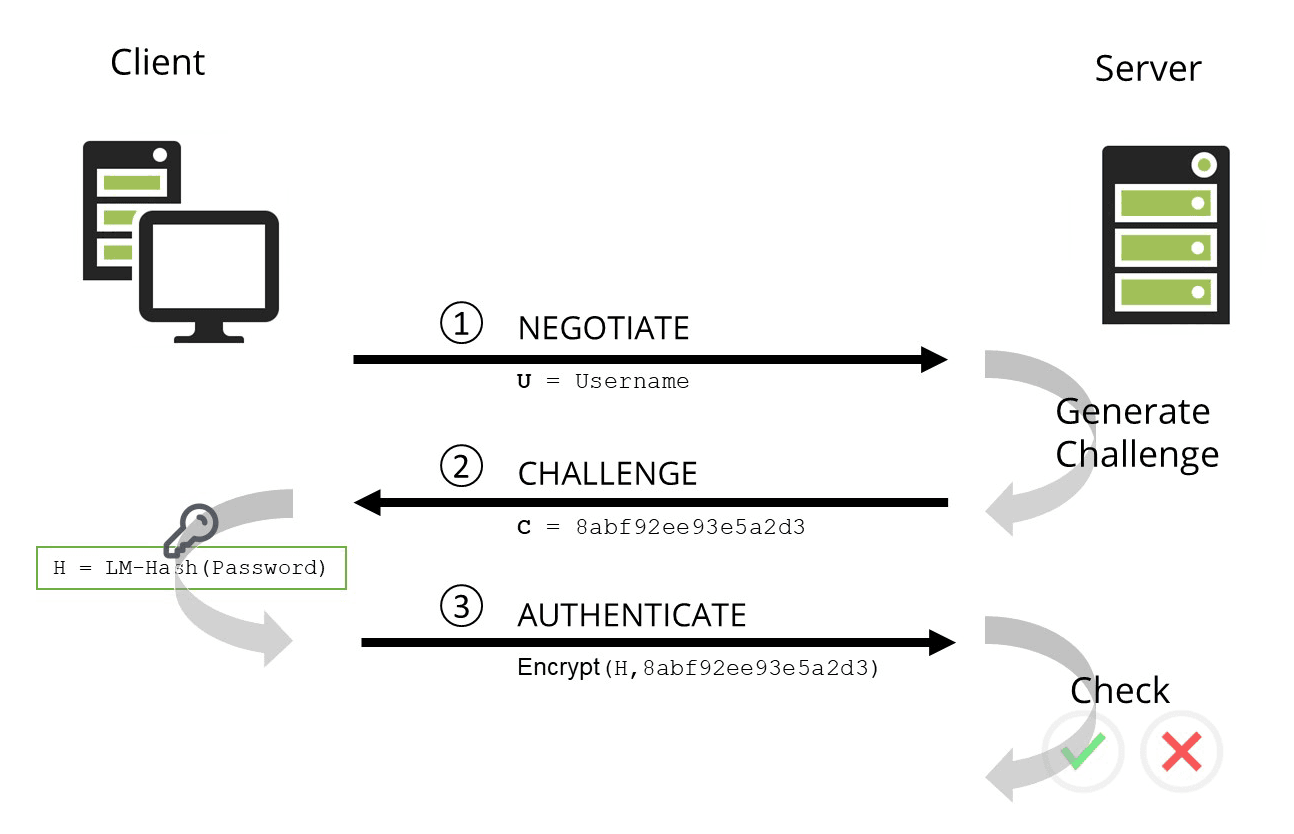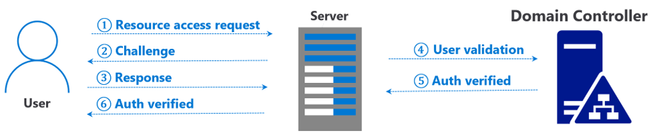
Azure ATP investigation of brute force and account enumeration attacks made over the NTLM protocol - Microsoft Community Hub

Azure ATP investigation of brute force and account enumeration attacks made over the NTLM protocol - Microsoft Community Hub

Professional Labs - Known #ADFS Brute Force security vulnerability : It allows brute-forcing all domain accounts from the external network, while bypassing the extranet lockout policy. This can easily lead to massive

NTLMRecon - Tool To Enumerate Information From NTLM Authentication Enabled Web Endpoints - GeeksforGeeks
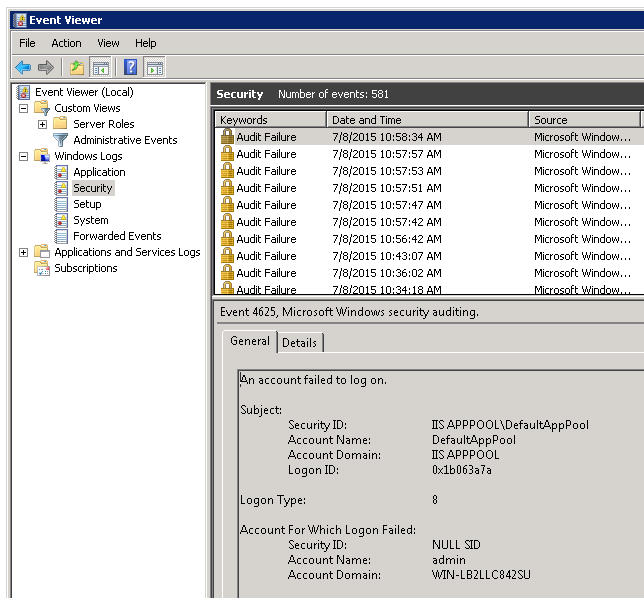
IIS Web Login Protection. Stop brute-force attacks on IIS Authentication methods - Basic, Digest, NTLM.