![Kishan Kumar - Web Security Topics for selfstudy [+] Cache Poisoning [+] Cash Overflow [+] Clickjacking [+] Command injection attacks [+] Comment Injection Attack [+] Content Security Policy [+] Content Spoofing [+] Kishan Kumar - Web Security Topics for selfstudy [+] Cache Poisoning [+] Cash Overflow [+] Clickjacking [+] Command injection attacks [+] Comment Injection Attack [+] Content Security Policy [+] Content Spoofing [+]](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=2549411185163312)
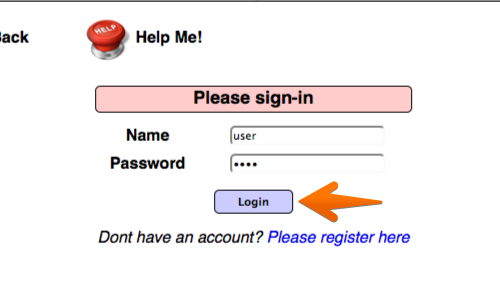
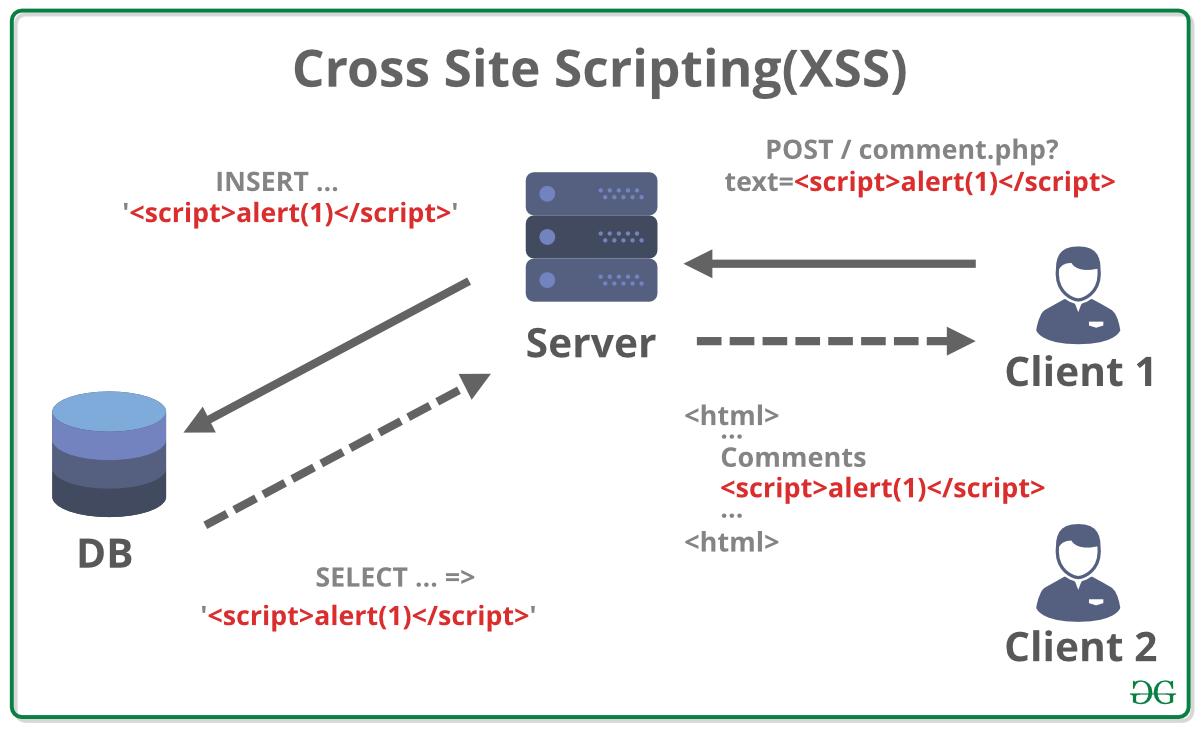
Kishan Kumar - Web Security Topics for selfstudy [+] Cache Poisoning [+] Cash Overflow [+] Clickjacking [+] Command injection attacks [+] Comment Injection Attack [+] Content Security Policy [+] Content Spoofing [+]

Non-Hermitian physics for optical manipulation uncovers inherent instability of large clusters | Nature Communications

Combating Information Manipulation: A Playbook for Elections and Beyond | International Republican Institute
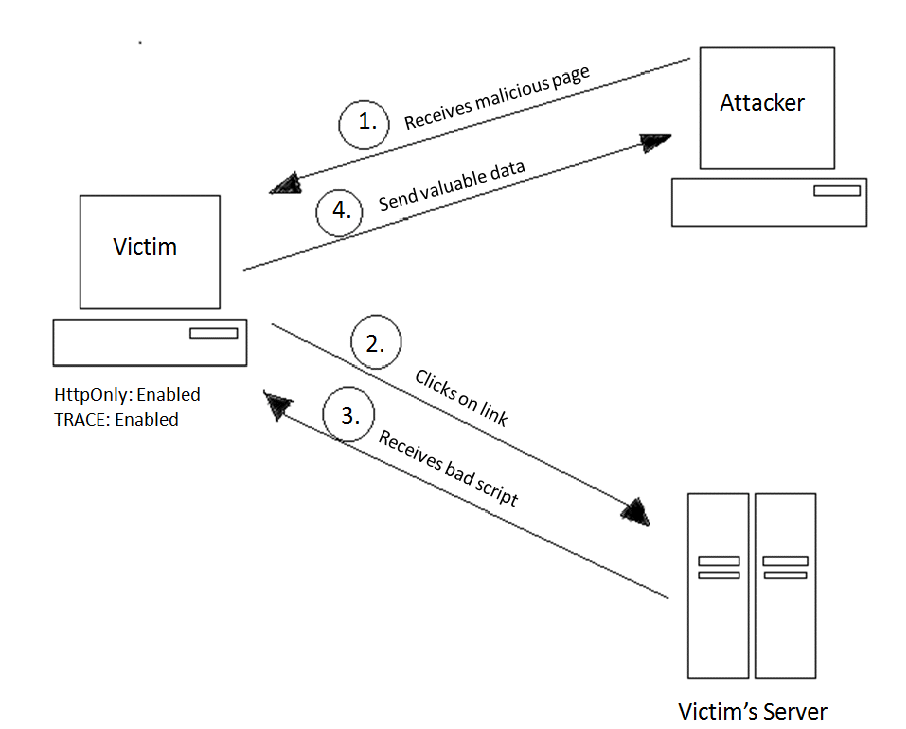
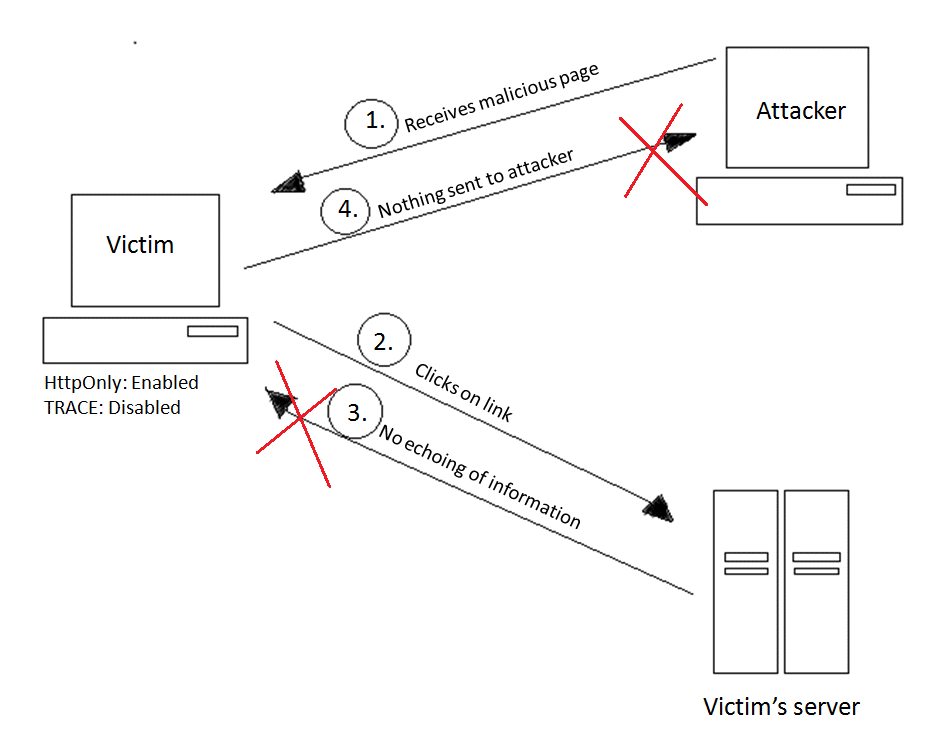
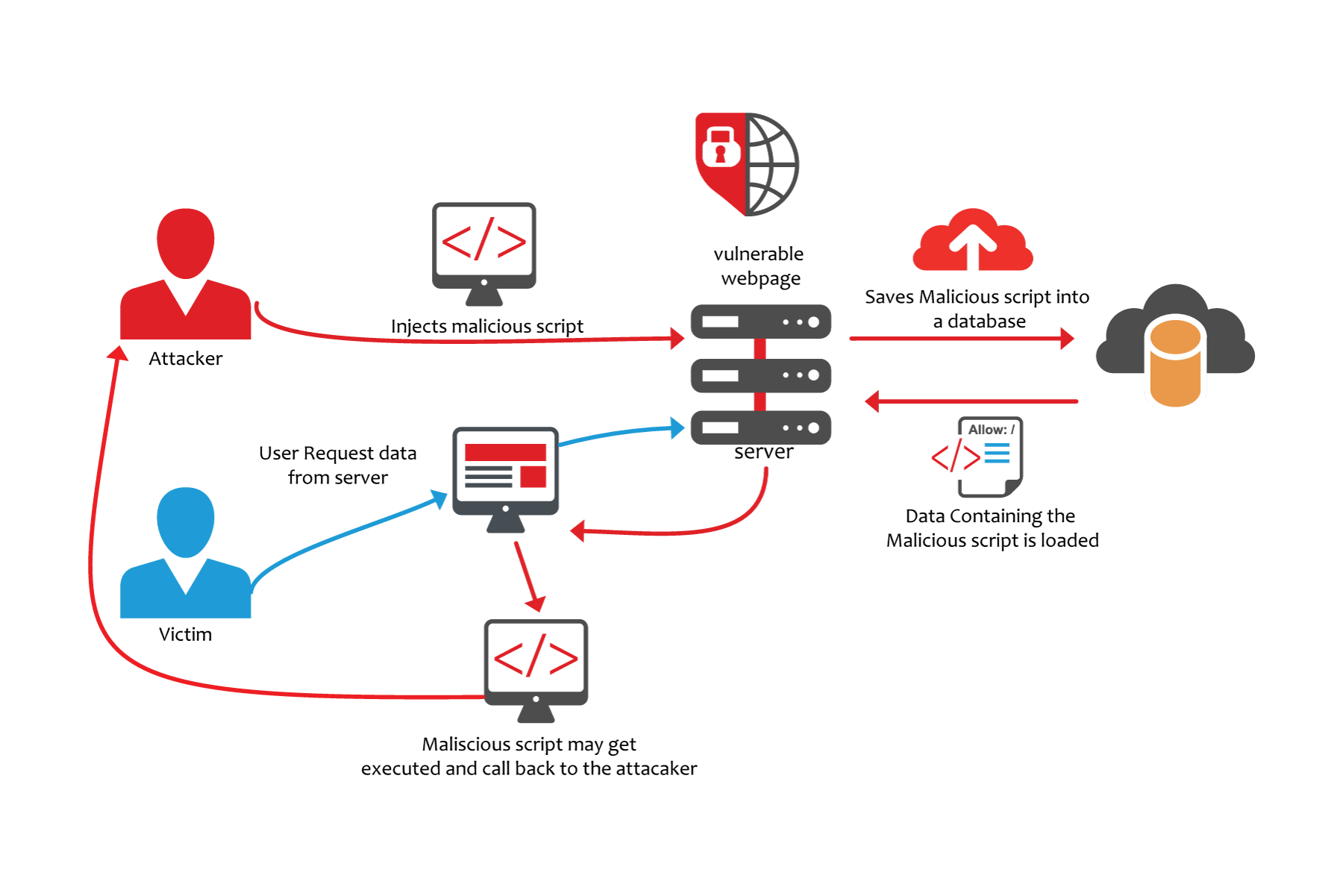
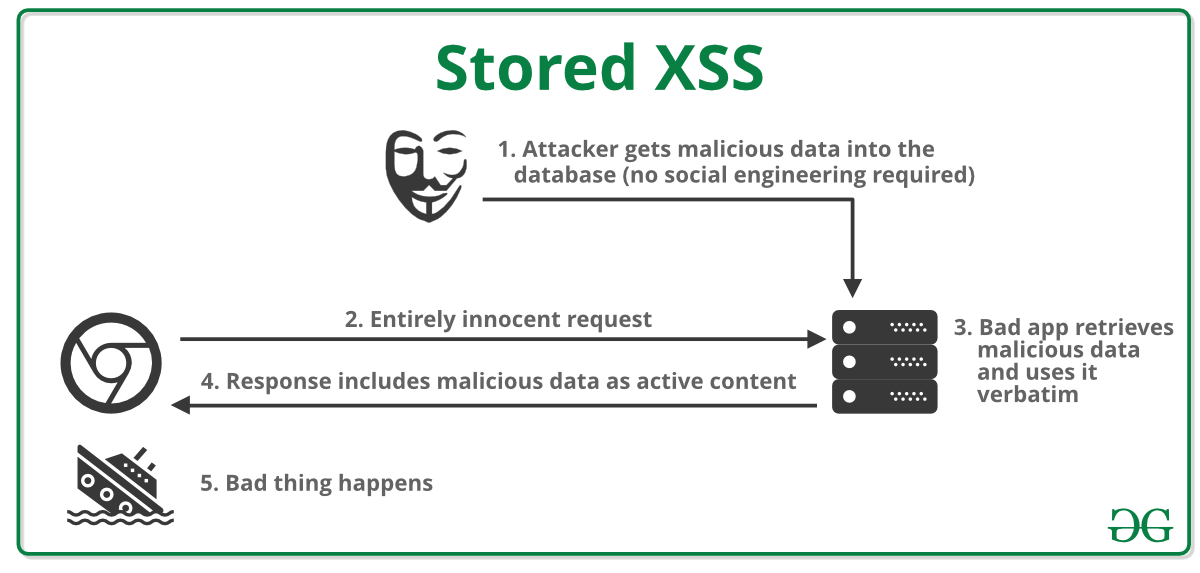
Securing Apache, Part 4: Cross-site Tracing (XST) & Cross-site History Manipulation (XSHM) - Open Source For You